What's the Buz: Forensic Analysis of Buz for iOS
- laurora4n6
- Apr 10, 2024
- 5 min read
Updated: Apr 11, 2024
A couple of weeks ago I was reading an article which mentioned the use of "walkie talkie" type apps. I was not aware these apps existed (enough with the old lady stuff 😂). So I went on the Apple App store and found two popular "communication" apps one is Zello, and the second is Buz. I chose to conduct testing on the Buz application.
On the Apple App store web page Buz-Communication Made Easy, promotes their application as "effortless voicechat on the go." The app works on iPad, iPhone, and Apple watch. Buz advertises that the app "allows you to effortlessly connect with family and friends. Stay connected through voice, even when your phone is locked."
Figure 1. Buz app icon. https://apps.apple.com/al/app/buz-communication-made-easy/id1628292843?platform=iphone
I conducted this testing with my test device;
iPhone 7, running iOS 15.8.2, model number MNAM2LL/A
I installed the Buz app version 1.28.0 and gave the app permission to access "contacts" and "microphone." Installation occurred on March 28, 2024 at 0926hrs. I then setup my account on March 28, 2024 at 1537hrs, username teresar, with this profile image.
Figure 2: Free image of Betty Boop. https://www.pinclipart.com/pindetail/ibiTmoi_betty-boop-transparent-background-free-png-images/
Device owner: Teresa Russel, trussel2024@icloud.com.
Carrier: Mint Mobile.
In my area of the US there has been a significant increase in organized retail theft and burglary. When I learned of these apps it occurred to me that this would be a great way for a burglary crew to communicate as attempting to text would be difficult. The fact this app works even when the device is locked makes it even more convenient.
I reached out to Ari and asked her if she would assist me in testing this app. Geraldine's test device owner's name is Ari. We arranged to test the app on April 2, 2024.
I chose a local outlet mall. The back story for this test is Teresa and Ari have been hired by a burglary crew to conduct physical surveillance on local outlet malls. Just as a burglary crew would do checking for security guards, stores in mall, entrances and exits, ease of access to delivery area. THIS IS A MOCK STORY.
I arrived at the local outlet mall (in the midwest) on April 2, 2024 at 0927. I enabled Location Services at this time. Teresa used the app to radio Ari who is located in southern US. Even with this distance the reception was very clear. To use is just like a radio the user holds the side button down and speaks. This app does work when the device is locked. Teresa asked Ari if she was there? Ari replied she was there. Teresa told Ari she was at a local outlet mall. Teresa took a picture of the Nike store in the mall, and sent image to Ari. Teresa walked around the mall radioing Ari for the next 11 mins.
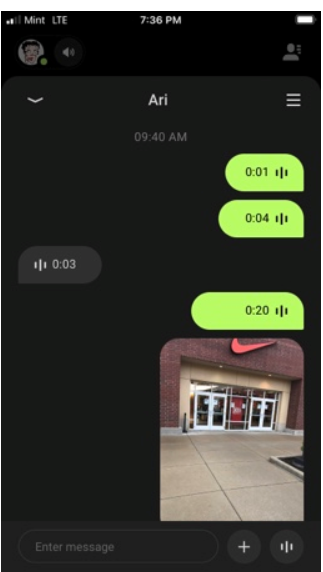
Figure 3. Screenshot of Buz app conversation screen.
The green audio clips are Teresa. The black audio clips are Ari. Ari used both the radio and sent text messages.
Figure 4. Screenshot of Buz app conversation on device.
The emoji in this next screenshot has an audio clip of laughter with it.
:
Figure 5. Buz app "voicemoji".
Ari and Teresa concluded their conversation at 0951hrs.
On April 2,2024 at 2018hrs. I collected a Quick image file using Magnet Axiom Process v. 7.10.1.39284, filename Apple iPhone 7 Quick Image.zip, file size 193MB.
TLDR: Both extractions, iOS backup and FFS have artifacts. As usual there are more artifacts in the FFS. Listed here are the folders of interest in the iOS backup. Here is the file path,
Apple iPhone Quick Image
>AppDomain-com.interfun.buz
>Documents
>IM5_US
>a94767967bc6e3e3122d98a75b789682
>IM5_Storage
>5373373583353653887
>im5.db (2 tables of interest, conversationlist, message
>IMVadRecordFile (contains user audio files of radio transmissions)
>Library
>WCDB
>5373373583353653887
>Database (table "ContactTable")
Files of interest in both backup and FFS;
Backup: im5.db, IMVadRecordFile, and Database
FFS; file path
\private\var\mobile\containers\data\application\A160F413-39BF-433C-97C9-4A00230AD62B
>Documents
>IM5_Files
>ReceivedFiles
>SendFiles
>IM5_Storage
>5373373583353653887
>im5db
>IMVadRecordFile
>Library
>com.hackemistSDImageCache
>default
>libpag
>TekiPlayerHighPriority
>WCDB
>5373373583353653887(userID, this number will vary)
>Database
If the examiner does a filter search by Relative Date/Time, Magnet Axiom Examiner reveals 44,013 artifacts. These include,
Biome Application Intents
Biome Application Launch
Installed Applications
InteractionC Interactions
KnowledgeC Application Focus
KnowledgeC Application Usage
KnowledgeC Device Lock States
KnowledgeC Notification Usage
Unified Logs
If the examiner chose to carve for Custom artifacts. Good news the im5db is parsed.
Custom Artifacts im5db "message".
***Now for the longer analysis report.
I then utilized Magnet Axiom Examine to analyze the image file. Magnet Axiom calls the logical image(backup) a quick image. This image type will only provide what the user observes on the device.
Magnet Axiom currently does not process the Buz app. My analysis was conducted through the file system.
I located AppDomain-com.interfun.buz this is the Buz app package name. Here are the folders available in a logical extraction:
Figure 6. Logical image folders for Buz app.
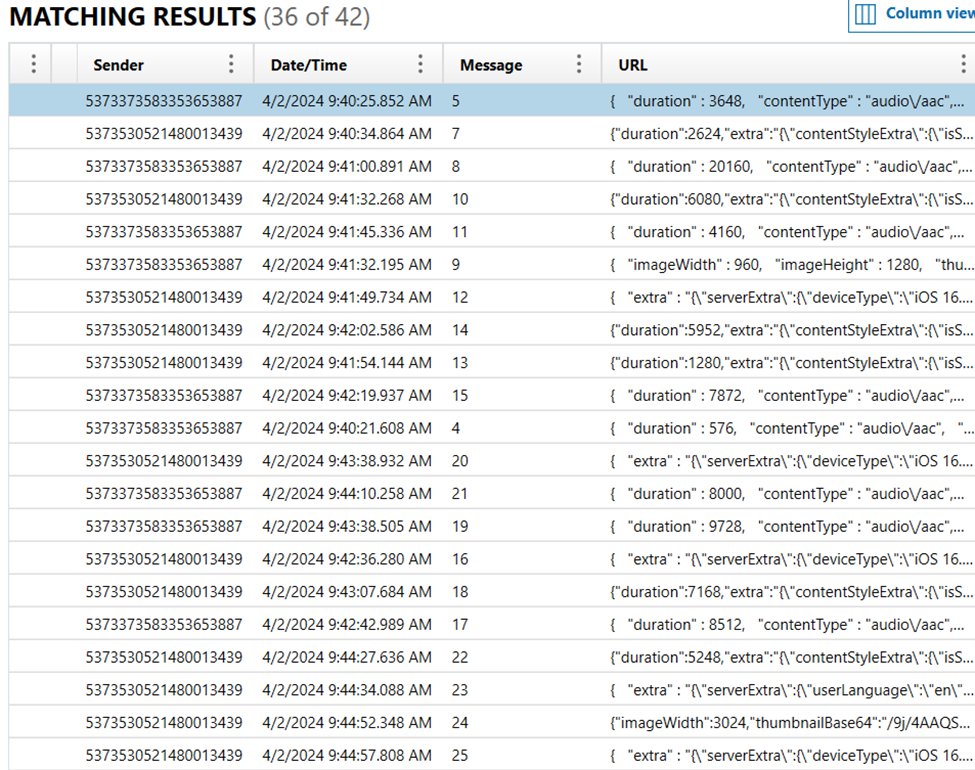
The folders of interest are; Documents>IM5_US>a94767967bc6e3e3122d98a75b789682>IM5_storage>5373373583353653887 (this number is the userID), this folder contains the im5.db. The two tables of interest are "conversationlist" and "message." The "conversationlist" table provides the app userID, and lastUpdateTime (in Unix milliseconds).
Figure 7. im5.db, table "conversationlist".
The "message" table contains the conversation including if text was received, and photos.
This table provides the fromId, createTime (Unix milliseconds), and pushContent.
Figure 8. "message" table #1
Figure 9. Second screenshot of "message" table.
The next folder of interest is the "IMVadRecordFile" this folder contains audio files of Teresa's radio transmissions. The audio files can be saved to an external folder and played with media player.
Figure 10. IMVadRecordFile folder containing audio files.
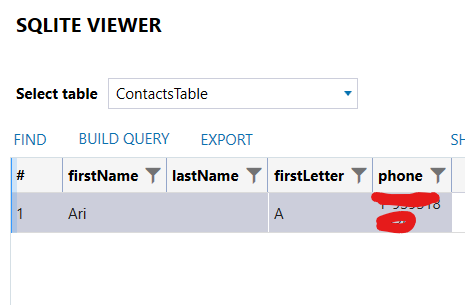
The last folder containing usable artifacts is Library>WCDB>5373373583353653887, which contains a Database file. The table of interest is "ContactsTable" Teresa only had one contact added which was Ari.
Figure 11. "ContactsTable" contents.
On April 7, 2024 at 1522hrs. I jailbroke the iPhone 7 using Palera1n, downloading Sileo package manager, and Filza File Manager package version4.0.1-3.
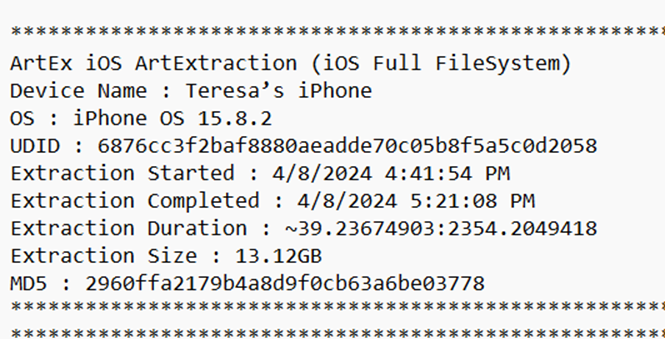
On April 8, 2024 at 1641hrs. I extracted a full file system from the jailbroken iPhone 7 using ArtEx version 2.8.0.9. Filename 6876cc3f2baf8880aeadde70c05a5c0d2058_Full_1.tar
Figure 12. ArtEx extraction information.
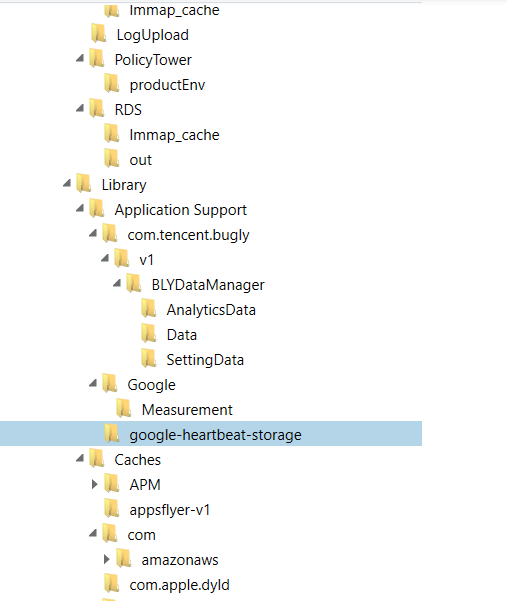
On April 9, 2024 at 0800hrs. I used Magnet Axiom Process v. 8.0.0.39753 to process the full filesystem file. Below is an image of all of the folders associated with the Buz app that are contained in a full filesystem extraction.
Figure 13. First screenshot of entire folders for Buz app in FFS.
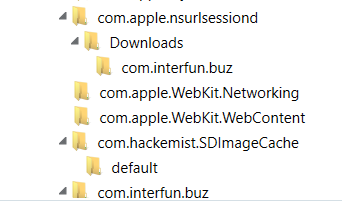
Figure 14. Second screenshot of folders in Buz app FFS.
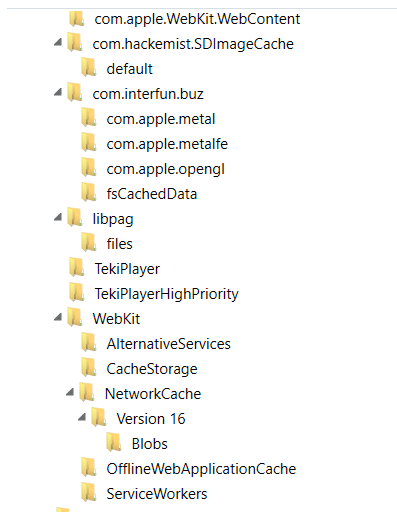
Figure 15. Third screenshot of folders in Buz app FFS.
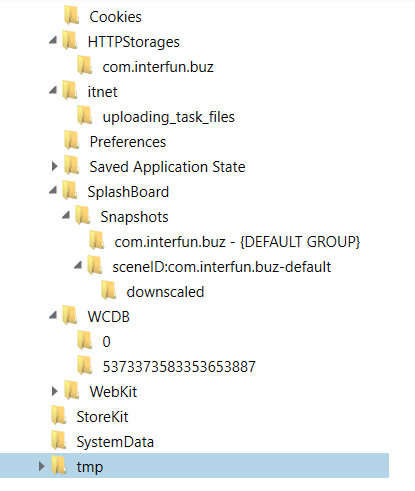
Figure 16. Fourth screenshot of folders in Buz app FFS.
Figure 17. Fifth screenshot of folders in Buz app FFS.
I will only mention the folders of interest that are not included in the logical extraction. First folder is IM5_US>IM5_Files>5373373583353653887>ReceivedFiles contains the audio files of Ari's radio transmissions. The audio files can be played inside Magnet Axiom Examine.
Figure 18. ReceivedFiles audio files of Ari's transmissions.
The SendFiles folder contains the two images Teresa sent to Ari.
Figure 19. Screenshots of SentFiles folder, containing two image
files sent to Ari, and images of the content of the two files.
Teresa’s Buz profile image located in Folder> com.hackemist.SDImageCache>default
Figure 20. Folder com.hackemist.SDImageCache, containing Teresa's Profile image.
Lastly, emojis in the Buz app are "voicemojis" as they have audio. The emoji sent by Ari to Teresa was the laughing emoji. The file contained in the screenshot below is audio of a laugh.
Voicemojis are located in libpag folder>TekiPlayerHighPriority.
Figure 21. Screenshot of folder TekiPlayerHighPriority containing audio file of voicemoji.
This concludes my report on the test of the Buz app. I hope you enjoy. My next project is to write a python parser for iLEAPP.
















Comments